CVE-2023-33621: GL.iNET Auth Token in GET Query String
CVE-2023-33621: GL.iNET Auth Token in GET Query String
- CVSS Score - 5.3, Medium (CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:N/A:N)
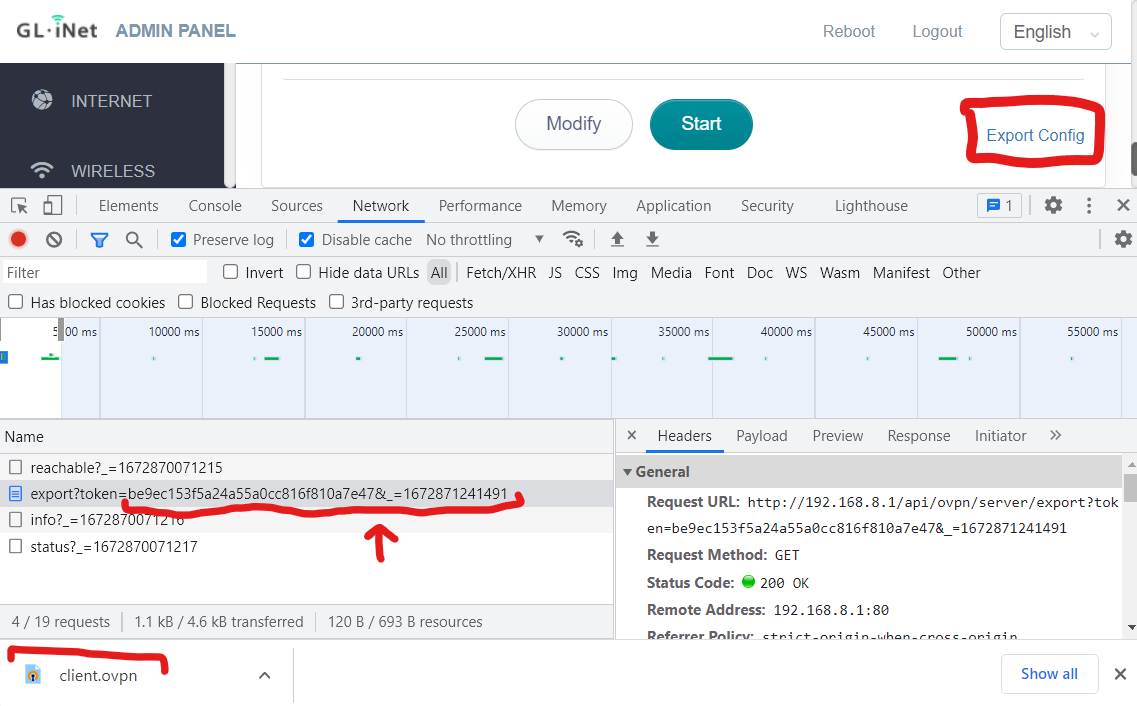
- Overview - When the OpenVPN server config is exported through the web GUI, the admin authentication token is passed through a GET parameter instead of the
AuthorizationHTTP header, meaning the token is more visible and has a greater chance of being stolen. - Description - Including sensitive tokens in the query string of GET requests can be a vulnerability (link1, link2, link3) since query strings are visible in various ways. For example, query strings are logged in web requests and proxies, can show up in browser history, and even in Referer headers when a third party is visited afterwards. The API is set to accept tokens through the
Authorizationheader, POST parameters, or GET parameters. Most of the requests made to the API put the token in theAuthorizationheader except for this one.
Fix
This was fixed in version 3.216.
PoC